防火墙后面的 tinc
示例:防火墙后面的 tinc
当在防火墙后面(而不是在防火墙本身上)运行 tinc 时,必须小心配置防火墙,以便允许 tinc 流量通过。此示例中包含示例防火墙规则。它们是为 iptables(Linux 2.4 防火墙代码)编写的,但已注释,以便您可以将相同类型的规则应用于其他防火墙。
示例:防火墙后面的 tinc
概述
运行 tinc 的主机的配置
tinc 的配置
防火墙配置
概述
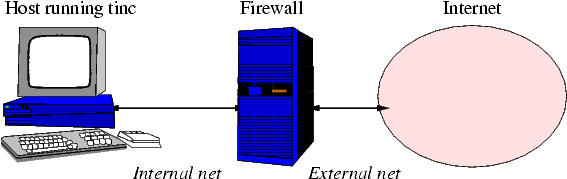
网络设置如下:
内部网络为 123.234.123.0/24
防火墙 IP 为 123.234.123.1
运行 tinc 的主机有 IP 123.234.123.42
主机想要连接的 VPN 的地址范围为 192.168.0.0/16
主机有自己的 VPN IP 192.168.10.20
请注意,内部网络具有真实的 Internet 地址,因此完全可以从外部访问(防火墙设置的限制除外)。如果内部网络具有私有地址,请参考伪装防火墙示例。
运行 tinc 的主机的配置
host# ifconfig
eth0 Link encap:Ethernet HWaddr 00:20:30:40:50:60
inet addr:123.234.123.42 Bcast:123.234.123.255 Mask:255.255.255.0
UP BROADCAST RUNNING MTU:1500 Metric:1
...
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:3856 Metric:1
...
vpn Link encap:Point-to-Point Protocol
inet addr:192.168.10.20 P-t-P:192.168.10.20 Mask:255.255.0.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
...
host# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
123.234.123.0 * 255.255.255.0 U 0 0 0 eth0
192.168.0.0 * 255.255.0.0 U 0 0 0 vpn
default 123.234.123.1 0.0.0.0 UG 0 0 0 eth0
host# iptables -L -v
Chain INPUT (policy ACCEPT 1234 packets, 123K bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 2161K packets, 364M bytes)
pkts bytes target prot opt in out source destination
host# iptables -L -v -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
tinc 的配置
host# cat /etc/tinc/vpn/tinc.conf
Name = atwork
ConnectTo = home
host# cat /etc/tinc/vpn/tinc-up
#!/bin/sh
ifconfig $INTERFACE 192.168.10.20 netmask 255.255.0.0
host# ls /etc/tinc/vpn/hosts
atwork home
host# cat /etc/tinc/vpn/hosts/atwork
Address = 123.234.123.42
Subnet = 192.168.10.20/32
-----BEGIN RSA PUBLIC KEY-----
...
-----END RSA PUBLIC KEY-----
host# cat /etc/tinc/vpn/hosts/home
Address = 200.201.202.203
Subnet = 192.168.1.0/24
-----BEGIN RSA PUBLIC KEY-----
...
-----END RSA PUBLIC KEY-----
防火墙配置
firewall# ifconfig
ppp0 Link encap:Point-to-Point Protocol
inet addr:123.234.123.1 P-t-P:123.234.120.1 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MTU:1500 Metric:1
...
eth0 Link encap:Ethernet HWaddr 00:20:13:14:15:16
inet addr:123.234.123.1 Bcast:123.234.123.255 Mask:255.255.255.0
UP BROADCAST RUNNING MTU:1500 Metric:1
...
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:3856 Metric:1
...
firewall# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
123.234.123.0 * 255.255.255.0 U 0 0 0 eth0
default 123.234.120.1 0.0.0.0 UG 0 0 0 ppp0
firewall# iptables -L -v
Chain INPUT (policy ACCEPT 1234 packets, 123K bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy DROP 1234 packets, 123K bytes)
pkts bytes target prot opt in out source destination
1234 123K ACCEPT tcp -- ppp0 eth0 anywhere 10.20.30.0/24 tcp flags:!SYN,RST,ACK/SYN
1234 123K ACCEPT any -- eth0 ppp0 10.20.30.0/24 anywhere
1234 123K ACCEPT tcp -- ppp0 eth0 anywhere 123.234.123.42 tcp dpt:655
1234 123K ACCEPT udp -- ppp0 eth0 anywhere 123.234.123.42 udp dpt:655
Chain OUTPUT (policy ACCEPT 2161K packets, 364M bytes)
pkts bytes target prot opt in out source destination
firewall# iptables -L -v -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
firewall # cat /etc/init.d/firewall
#!/bin/sh
echo 1 >/proc/sys/net/ipv4/ip_forward
iptables -P FORWARD DROP
iptables -F FORWARD
iptables -A FORWARD -j ACCEPT -i ppp0 -d 10.20.30.0/24 -p tcp ! --syn
iptables -A FORWARD -j ACCEPT -i eth0 -s 10.20.30.0/24
iptables -A FORWARD -j ACCEPT -i ppp0 -o eth0 -d 123.234.132.42 -p tcp --dport 655
iptables -A FORWARD -j ACCEPT -i ppp0 -o eth0 -d 123.234.132.42 -p udp --dport 655
